Ask Professor Puzzler
Do you have a question you would like to ask Professor Puzzler? Click here to ask your question!
Hi, I want know about 2-tier architecture and 3-tier architecture. Please explain me with some examples. Regards, Chandra
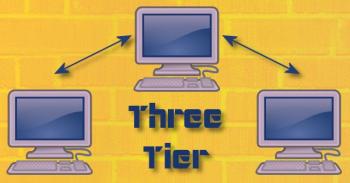
Chandra, The easiest way to explain this is, as you suggest, by an example. So I'll give you an example.
Let's suppose I'm going to write a piece of software that students at a school can use to find out what their current grade is in all their classes. I structure the program so that a database of grades resides on the server, and the application resides on the client (the computer the student is physically interacting with).
When the student wants to know his grades, he manipulates my program (by clicking buttons, menu options, etc). The program fires off a query to the database, and the database responds with all the student's grades. Now my application uses all this data to calculate the student's grade, and displays it for him.
This is an example of a 2-tier architecture. The two tiers are:
- Data server: the database serves up data based on SQL queries submitted by the application.
- Client application: the application on the client computer consumes the data and presents it in a readable format to the student.
Now, this architecture is fine, if you've got a school with 50 students. But suppose the school has 10,000 students. Now we've got a problem. Why? Because every time a student queries the client application, the data server has to serve up large queries for the client application to manipulate. This is an enormous drain on network resources. So what do we do? We create a 3-tier architecture by inserting another program at the server level. We call this the server application. Now the client application no longer directly queries the database; it queries the server application, which in turn queries the data server. What is the advantage to this? Well, now when the student wants to know his final grade, the following happens:
- The student asks the client application.
- The client application asks the server application.
- The server application queries the data server.
- The data server serves up a recordset with all the student's grades.
- The server application does all the calculations to determine the grade.
- The server application serves up the final grade to the client application.
- The client application displays the final grade for the student.
It's a much longer process on paper, but in reality it's much faster. Why? Notice step 6. Instead of serving up an entire recordset of grades, which has to be passed over a network, the server application is serving up a single number, which is a tiny amount of network traffic in comparison. There are other advantages to the 3-tier architecture (for example, a three tier architecture allows you to do load balancing, by having multiple servers that can function as the middle tier).
Incidentally, this website is a 3-tier application. The client application is your web browser. The server application is the php code which queries the database (the third tier) for the question-and-answer you requested. I hope that helps!
Historical note on this blog post: This question was originally asked and answered in 2005 - more than a decade ago! It became one of the most popular pages on the "Ask Doug" blog, and began circulating widely on the internet. As it went along, portions of it were modified, garbled, or even deleted, until eventually it came to the attention of those kind folks at Snopes, who wrote an article about this article, verifying the information within it. Imagine my surprise when one day my wife received her weekly Snopes e-newsletter, and at the top of the e-mail was my blog post!
The blog post has been moved to the "Ask Professor Puzzler" blog as part of our process of consolidation.
Question: I got an email from my * company, and it talked about logging in at their 'secure site', and it mentioned https and http. What is that?
Answer: HTTP stands for HyperText Transport Protocol, which is just a fancy way of saying it's a protocol (a language, in a manner of speaking) for information to be passed back and forth between web servers and clients. You really don't need to know what it all stands for; the important thing is the letter S which makes the difference between HTTP and HTTPS.
The S (big surprise) stands for "Secure". You probably didn't need me to tell you that, because you already knew it had something to do with security. If you visit a website or webpage, and look at the address in the web browser, it will likely begin with the following: http://. This means that the website is talking to your browser using the regular 'unsecure' language. In other words, it is possible for someone to "eavesdrop" on your computer's conversation with the website. If you fill out a form on the website, someone might see the information you send to that site.
This is why you never ever ever enter your credit card number in an http website!
But if the web address begins with https://, that basically means your computer is talking to the website in a secure code that no one can eavesdrop on. You understand why this is so important, right? If a website ever asks you to enter your credit card information, you should automatically look to see if the web address begins with https://.
If it doesn't, there's no way you're going to enter sensitive information like a credit card number!
It should be pointed out that just because a website has that magic "S" in its address, that does not mean it is wise to do business with them; even scam artists can have https sites! It simply means that no outsiders can eavesdrop on your conversation...doesn't mean you should be having the conversation in the first place. Only do business with reputable firms, or firms you have thoroughly checked out!
I heard someone talking about the "Diameter of the Internet" recently. I understand finding the diameter of a circle; it's just the distance across its widest point. But what is the diameter of the internet, and how do you measure it?
Note: this item was originally posted on the "Ask Doug" blog* back in 2005. We've updated it and republished it with additional commentary at the bottom.

Have you ever played the game "Six Degrees Of Separation"? You start out with a person (often a movie star), and then see if you can relate them to another movie star in six or less connections. For example, how would you connect Julia Roberts to Sean Connery? Well, Julia Roberts starred with Richard Gere in "Pretty Woman", and Richard Gere starred with Sean Connery in "First Knight". That's two degrees right there.
The internet diameter is similar. How many degrees of separation are there between any two randomly selected web pages? How many clicks does it take to get from one web page to another? Researchers have done studies and calculations to try to determine the answer to this question, and the average "distance" in clicks between any two web pages is known as the diameter of the web. As of the turn of the millenium, the diameter of the internet was approximately 19 clicks.
And here we are in 2016, and you'd think we'd have updated statistics for you.
We don't.
We have some wrong statistics, though. Because, like everything else on the internet, people read what they want to read, and interpret things how they want to interpret them, with no regard for reality.
For example, in 2013, Smithsonian Magazine's website (yes, you read that right - I'm accusing Smithsonian of publishing bogus statistics - although, to be fair, they did partially retract their article) stated this information as though it was new, and reworded it to say that the maximum distance in clicks was 19. (Go back and read the original post; 19 was the average distance, not the maximum distance).
Others have made even more remarkable claims, such as "The diameter of the internet will never exceed 19."
But the reality is, nobody seems interested in continuing this line of study, and there doesn't appear to be any current statistical analysis on the diameter of the internet. So I guess we might as well keep saying the diameter is 19, even though that statistic is now about 16 years old!
There are some questions that would be fascinating to explore (if only I had more time!). Questions like:
- How do you deal with a website that is completely isolated (no inbound or outbound links)? Surely their distance to other websites isn't defined to be infinite? Because that would be problematic for averaging purposes! I suspect sites like that are dismissed from the equation.
- Did you realize that "distance" is not a "commutative" property? In the real world, if we say the distance from A to B is five miles, that means the distance from B to A is also five miles. But in the web, between any two points there are two distances - the number of clicks by outbound links from A to B, and the number of clicks by outbound links from B to A. These two numbers can be significantly different. To see why this is so, consider that there are thousands of websites around the world that link to The Problem Site. This gives a distance of one click. But The Problem Site doesn't link to most of those sites, which means the distance has to be more than one click. In fact, we should really think of it like distances between two cities when all the roads are one-way streets, so you have to take a different route from A to B than you would from B to A. So how do you calculate the distance? Do you take the smaller number? The larger one? Or the average?
- How are search engines included in the mix? Technically, Google links to virtually every website. But the pages that link to various sites are not static, because they are dependent on user input to display the links. On the other hand, if I search for "The Problem Site" on Google, and post the link here, I've now provided an indexable link for people to use when calculating the internet diameter. So have I changed my click distance to google by doing that?
Those are the questions that keep me up at night when I'm pondering 16-year-old statistics that no one else seems to care about any more!
Professor Puzzler
* The "Ask Doug" blog was the precursor to the Ask Professor Puzzler blog. We are gradually moving the content from that blog to this location. Most items will be kept to their original publication dates, but occasionally, when we find an item of special interest, we'll re-post it with the current date, so our visitors will be more likely to find it!

Emmanuel from Nigeria asks, "How are letters converted into binary codes?"
Well, Emmanuel, I'm guessing you came here from our Binary Coding Page. If so, you ask an excellent question, because the subject of how we convert letters is not really explained there.
The big question is, "How do you convert a letter to a number?" Because if you can convert the letter to a number, then you can use the information on our base conversion page to convert that number into binary. So how does the computer do the conversion from letter to number?
There is a standard listing called the "ASCII Character Set," in which every character used on a computer's keyboard is assigned a number. There are a lot of these characters, because there isn't just one for every key on your keyboard - there's also one for each key with the SHIFT key pressed. The ASCII character set has room for 256 characters, numbered from 0 to 255.
You might wonder, "Why 256?" and the answer is, because 256 = 28, which means anything less than 256 can be written as 8 binary bits (place values). Each character needs to have the same number of binary bits - otherwise nobody would know where one character ends and the next one starts. So even though the number 15 only needs four bits to be written in binary (1111two) in order to make sure all the numbers have the same length, the computer would write it as 0000 1111two. We put a space between every four digts, for the same reason that we do commas in base ten - it helps us read long strings of digits more easily.
Okay, so with that out of the way, now we just need to know what letters are represented by what number. Here's a quick reference for you:
A = 65
B = 66
C = 67
...
X = 88
Y = 89
Z = 90
Remember I mentioned that the ASCII Codes account for the shift key? That means that lower case letters have a different number assigned than upper case letters:
a = 97
b = 98
c = 99
...
x = 120
y = 121
z = 122
Now, there are a couple things you might have wondered about, like "What comes before 65?" and "Why is there a gap between the upper and lower case numbers?"
The answer to the first question is, there are other characters in those gaps - numbers, punctuation, special control characters (like the Backspace, Enter, Delete, etc).
The reason there's a gap between the upper case and lower case alphabets is that it makes "a" 32 more than "A." That is very convenient because 32 is a power of 2 (25), so changing between upper and lower case means changing just one bit:
A = 0100 0001
a = 0110 0001
So if you're using the computer's ASCII character set, and you wanted to convert "Hello" into binary, you would look up each letter in the ASCII chart:
H = 72 = 0100 1000two
e = 101 = 0110 0101two
l = 108 = 0110 1100two
l = 108 = 0110 1100two
o = 111 = 0110 1111two
So the entire word "Hello" is:
0100 1000 0110 0101 0110 1100 0110 1100 0110 1111two.
BUT...you don't have to use the ASCII conversion; you could create your own way of converting letters to numbers. Why would you want to do that? Well, you probably wouldn't, unless you wanted to conserve space, and you didn't care about anything except the basic upper case alphabet.
You see, if all you cared about was the upper case letters (and maybe a space), then you could do a conversion like this:
SPACE = 0
A = 1
B = 2
C = 3
...
X = 24
Y = 25
Z = 26
Why would you want to do that? Because now your biggest number you need to encode is 26, which is less than 25. That means that you only need five digits to write each number instead of eight! So your encoded message will take up 5/8 as much space. You'll save about 38% of the space on the page.
Since you have to have space in your table for 32 characters, and you've only used up to 26, you might as well use the other ones. Maybe include some punctuation?
COMMA = 27
PERIOD = 28
QUESTION MARK = 29
DASH = 30
DOLLAR SIGN = 31
Or you could create a table with 64 characters, which would either let you put in a lot more punctuation, or the numbers, or the lower case alphabet. But now you're using six binary digits per character, so you're not saving as much space.
Or you could completely jumble your character chart, which makes it a harder for other people to decode:
A = 17
B = 3
C = 25
etc...
But if you really want to make a coded message, there are much better ways to do it, so everyone just sticks with the standard ASCII codes in order to keep things simple.
A couple more things:
- The ASCII chart is available online; just go to google and search for "ASCII codes" and you'll get the entire list!
- ASCII stands for "American Standard Code for Information Interchange"
Thanks for asking, Emmanuel. I probably gave you much more information than you were expecting, but I hope you found it both interesting and helpful!
Professor Puzzler
PS - you can find more information about encoding here: Colors, Numbers, and Graphemes.
I get file attachments from both friends and strangers. Should I just open the ones from friends?
I would even think twice before opening file attachments from friends. What if your friend's computer has been infected by a virus, and the virus emails you a message with itself attached? You get the email, think it's from your friend, and open the attachment. *Poof!* Your computer is now infected!
The only time you should open an attachment even from a friend is if it is a file type that can't carry viruses (generally speaking you can open image files, but even with those, believe it or not, someone developed a virus to attach to an image (read below for a question and answer about that).
If you have any doubt about whether a file type can carry a virus, don't open the email. Call or email your friend and say "Did you send me this file?" If they say no, obviously you aren't going to open it. And if the message is from a stranger? Don't open it at all! I occasionally get resumes from people who want to work for me, and rather than mailing them, they send them as Microsoft Word Documents. I don't know them from Adam, and I won't open their attachments.
I get emails with picture files (stuff with .gif?x=5, .bmp, and .jpg?x=5 file extensions) attached. I know there are some kinds of email attachments I should never open; what about these? Can I get infected through these?
Well...yes, technically, it is possible, but only under the following scenario. Your computer has to already be infected with another virus whose purpose is to act as interpreter for the image virus. Seems kind of pointless to me. (The "Perrun Virus" was an example of this kind of virus, which attached to jpg files. A lot of hype, not much action)
However, you still need to be careful when opening images attached to emails. Be sure that the file extension really is an image extension (the ones you listed, plus a few others). I've seen emails come in with file names like "yourpicture.jpg?x=5.exe". Clever. The extension isn't really 'jpg', it's 'exe', and you already know you should never open those. And remember: if the attachment is from someone you don't know, why would you bother opening it anyway?

